 Summary: As security breaches rise, enterprise web application security is an increasingly important topic. You must stay ahead of evolving security trends in order to keep your data and applications safe. How will web application security evolve in the coming year? What web application security threats can we expect in the near future? In this article, we explore web application security trends of the near future and explain why they’re important.
Summary: As security breaches rise, enterprise web application security is an increasingly important topic. You must stay ahead of evolving security trends in order to keep your data and applications safe. How will web application security evolve in the coming year? What web application security threats can we expect in the near future? In this article, we explore web application security trends of the near future and explain why they’re important.
Security breaches are on the rise. Sensitive data gets compromised on a seemingly daily basis. These breaches create negative publicity, and lead to huge financial losses.
Can you guess which aspect of your business systems hackers target the most? As mentioned in this article: “According to numerous studies, the preferred method for attacking businesses’ online assets is via their Web applications.” What’s worse, a recent report found that over half of all web applications suffer from commonly known vulnerabilities.
As more data moves to the web, and businesses create more web applications, this threat is only increasing. How can you protect your business applications?
The first step: Recognize the risks, and stay ahead of the curve. Understand where web application security is now, and where it’s heading. Do you know what application security threats we can expect in the near future? Do you know how web application security evolving?
Today, let’s answer these questions. While the list could certainly be longer, here are 5 important trends in web application security to watch for in the near future.
1. Increased application demand leads to vulnerable applications
In a recent article, we examined an unsettling fact: Most business applications still suffer from commonly-known security flaws. We’re not talking about new vulnerabilities. We’re talking about commonly recognized–and easily fixable–security flaws that businesses have known about for over a decade.
What’s more, these threats can create irreparable damage to a business.
Why? We explored a few reasons in the article mentioned above, but there’s one overriding issue. There’s an increasing demand for new business applications–a trend that will only grow. More and more, the demand outpaces the organization’s ability to create them.
As a result, we’re seeing two things happen. First, we have an increased number of new developers, rushing to meet project deadlines. In the struggle to meet these deadlines, security suffers.
Second, we have more development outsourced. As explained below, this becomes a problem when the outsourcing firm doesn’t understand the organization’s security needs.
“The desire by many businesses to build and launch new apps has outpaced these organizations’ ability to staff application development teams,” explains Ben Desjardins, Security Expert at Radware. “The result is a trends towards outsourced application development, often leveraging inexperienced development shops following abstract requirements with limited understanding of the security requirements that may exist in various industries or for particular use cases. This often leads to fundamentally insecure apps that are prone to the myriad attack tools available that find and exploit known vulnerabilities in underlying application components.”
2. Unsanctioned cloud apps create a larger security risk

Another problem created by the growing application demand: Shadow IT. Now, this isn’t a new trend, but it is on the rise. As its growth continues, we can expect it to greatly impact security.
What’s happening? End users are bypassing the IT department in favor of third-party, cloud-based solutions. Rather than waiting around for a solution from IT, they can now pull out a credit card and get up and running that day.
While this sounds great from a business user perspective, it creates a problem. This practice takes company data outside of the IT department’s control. When employees purchase and use third-party solutions, IT cannot manage and secure the data. Worse yet, they cannot evaluate the solution’s security.
What can you do about it? We won’t get into all the details here, as we covered a few ways to address Shadow IT in a previous article. But, do not ignore the problem. As explained below, it’s running rampant, and will continue to grow worse.
“In the future, we should expect more threats coming from unsanctioned cloud apps: On average 730 unsanctioned apps get connected to corporate cloud and used in an organization for a large spectrum of business activities,” says Adam Moisa, the CEO and Co-Founder of Compaaslabs.com. “This figure is even more frightening if we think that 94% of these apps are not enterprise-ready, leading to 95% of data exposure due to employee negligence.”
3. Stolen credential attacks rise
As people place more and more of their information online, stolen credential attacks are on the rise. Why is this so important? Stolen credential attacks can completely nullify all of your security efforts.
How so? As you know, many users have awful security habits. They reuse their login credentials across many sites. So, if a hacker gets a hold of one of your user’s credentials for one site, chances are good that they can access other applications as well.
“For many years, attackers have employed tricks such as cross-site scripting (XSS) and SQL injection (SQLI) to attack web sites,” says Mark Huss, senior consultant at SystemExperts. “Although these still are in regular use, the landscape is changing; stolen credentials now account for over half of all web attacks. This is an understandable progression – why fight to come up with a clever injection attack when credentials and credit card information are available in mass quantity, and cheaply? In addition, web browsers are getting better at defending against scripting attacks, and long-time targets such as Adobe Flash are falling out of favor.”
4. Two-factor authentication becomes a must in the enterprise
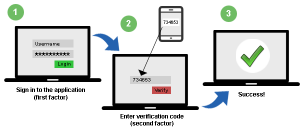
One way to fight the stolen credential attack: Set up two-factor authentication on your business applications. What is it? I’ll briefly explain the concept here, but you can read more about two-factor authentication in this article.
In short, it adds a second level of security to an account login. Rather than identifying a user with a single factor (username/password), it adds a second identification factor to the login process–usually a pin number delivered via sms to the user’s mobile device. It’s designed to maintain security, even if a user’s login credentials are compromised.
Now, two-factor authentication is not a new trend. It’s already used in popular web services like Gmail, Twitter, Linkedin, etc… However, it’s sparsely used in the business world. But, with the rise of security breaches, two-factor authentication is quickly becoming a must-have in the business world.
“One trend that is noticeable is role-based authorization and multi-factor authentication, with significant focus on secure session management,” says Balaji Jayaraman, DevOps Head at Chargebee. “Multi-factor authentication is becoming a standard in order to access sensitive and critical data that builds a kind of layered defense for preventing unauthorized access to applications or physical devices. Role based authorization makes sure the access is restricted to necessary roles which will minimize the scope even when targeted.”
5. The security skills gap drives the growth of third-party tools
Businesses often approach security with a false assumption. They assume that their developers understand security, and will build it into their applications.
Now, that’s true to an extent. A developer will understand the security basics. But, you can’t assume your developers are security experts. Their job centers around developing applications–often with a tight deadline.
Can they possibly compete with hackers who spend their days trying to attack web applications? Of course not.
The fact is, we’re facing a security skills gap. Most companies do not have the personnel in-house to create truly secure applications. As security breaches increase, we’ll see more and more businesses turn to third party tools to bridge this gap.
“The future of web application security lies with third party tools. The vast majority of web developers are NOT security experts and will continue to make mistakes that leave the door open to hackers,” says Yaron Guez, Chief Software Architect at Crypteron. “By adopting third party developer tools and security platforms, developers will harden their web applications while avoiding re-inventing the wheel and saving months of time. This is in line with the trend toward the cloud in general. Just like developers don’t have to build and maintain their own fleet of servers anymore, instead relying on Amazon, Microsoft and Google for their infrastructure concerns, the move towards security tools and platforms is following a similar path.”
Summary
These are just 5 trends in web application security, but the list could certainly be much longer. If you would like to add anything to this list, I’d love to hear it. Feel free to share in the comments.
Thank you for sharing important Information Trends of 2016 and beyond. As a mobile app developer i always looking for such blog that make me up to date with current trends and news. thank you again for this wonderful post.
Thank you for the sharing of your knowledge about Web Application security. I was writing my thesis for master degree about web application vulnerability testing in Ghana. Your article was informative for me. Thanks!